Discover how Millgate delivers complete solutions for our clients, helping them succeed
Home / Solutions & Services / IT Services in Sheffield
Our in-house IT services are bespoke to solve whatever tech challenge you face.

The pace of tech development is faster than ever. We understand the difficulty of managing an IT network across office, home and hybrid environments, which is where Millgate can help.
Our IT services portfolio develops alongside our clients, ensuring we provide a range of services that deliver real business benefits. We aren’t just a team of technicians on-hand when the network is down; we can actively work in the background to service and support your infrastructure.
Our first-class IT support services are bespoke for your business and designed for your success.

Let Millgate do the hard work for you. Whether you want to outsource all of your IT management, or just one aspect, we will create a bespoke solution that fits the needs of your business.

Providing remote and onsite support for your hardware and software, wherever your people are based, including guaranteed fix SLAs of up to 2 hours.

Seamlessly and safely integrate your business to the cloud in a network that incorporates an array of applications. This way, you can communicate and scale however suits you best.

Our team of experienced cabling engineers provide design and installation services for any structured cabling requirements. We also provide installation and deployment of Audio-Visual and CCTV tech products.
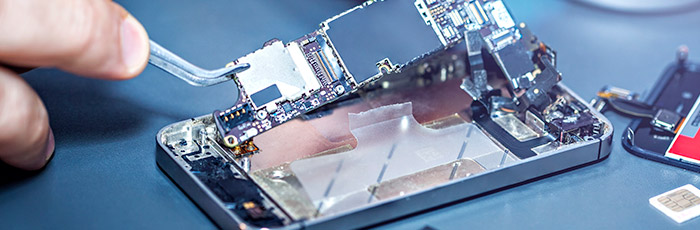
Accidents will happen from time to time, and we understand that getting your device back into working order is a critical requirement for any IT team. Our Device Repair team ensure your devices are up to industry standards with UK-wide collection and delivery and buffer stock replacement to eliminate downtme. Find out more.

Our secure build centre facility provides you with peace of mind, knowing that any items that are configured prior to delivery will have passed rigorous quality tests. Save time setting up your people for success.
Millgate offer IT assessment and health check services for your satisfaction, so you can know how effectively your tech is working.
All of our assessment services are tailored to your exact requirements. Using leading technologies and an in-depth approach, each assessment provides comprehensive reporting and documentation.
Keep your hardware healthy and look after your assets with Millgate. Our single-point IT maintenance accountability makes fixing those frustrating hardware problems easy.
Looking after networks is a full time job, so allow Millgate to do it for you. We’ll take it off your hands, and our strategic approach ensures any issues are dealt with immediately.
You only have one chance to recover lost data. Millgate’s 20+ years of experience and expert knowledge means you can rest easy knowing recovery will be done the right way.
Concentrate on your business whilst Millgate manages and develops your IT systems and processes, without any hassle for you.
Utilise the benefits of highly scalable cloud resources to consolidate your onsite infrastructure.
Protect your business data and systems with our adaptable and secure cloud services.
Our solutions scale from the home desk to the datacentre, providing cost effective support and maintenance of your systems.
Millgate helped SMPE develop an IT infrastructure project for their new building in Poland through our trusted partnership.
Millgate work in partnership with Vixsoft to provide their clients with exceptional service and support.
St Columba’s College was undergoing renovation, meaning a new cabling infrastructure was required in specific buildings along with new IT hardware in order to create an up-to-date learning environment for students.
Advantages to Structured Cabling
Achieve greater business continuity in the cloud
Why you need IaaS for your business.
Still using ISDN lines? Don't wait to migrate.
Call our friendly team today or request a call back for a more convenient time